Emails from recruiters are not safe
andrew@paon.wtfYou open your laptop and read the following email.
Hi <DEVELOPER>
Wow! Great Linkedin! I was particularly impressed by your <ANCIENT ITEM FROM WORK HISTORY>.
I'm a recruiter with fastqr.codes. We are tackling some of the industry's biggest challenges. I think you would be a great fit for <ABSURDLY JUNIOR ROLE>.
If this sounds interesting, check out our careers page.
-Andrew
This could be interesting. You haven’t heard of fastqr.codes before, so let’s see what it is.
You move your mouse to the careers link, and if you are unusually perceptive, you notice this URL in the bottom of your window before clicking:
https://my-fake-tracker.paon.wtf/item/1
Weird. Unless you are also unusually paranoid, you click on the link anyway and end up looking at fastqr.codes.
Tracking links
Of course, the URL you noticed is used for tracking. Here is how it works.
The recruiter drafts an email that includes links to various resources that their prospect (you!) might be interested in. Before sending the email, they replace all links with intermediary URLs that redirect to the original links.
The URLs that appear in the final email that you see are unique to you.
The recruiter might send basically the same email content to you and your peers, but the URLs that the links point to are different.
When you click on a link, the tracker service updates a database record to note that you have visited the link. It then redirects your browser to the actual site you want to visit.
This means the recruiter knows exactly which links you clicked on in their email, even if you intentionally never respond to them.
This kind of tracker service is also known as a bouncer, and the act of tracking people through a bouncer is called bounce tracking. There is surprisingly little information online about bounce tracking; much of what does exist can be found on Brave’s blog.
Tracking images
We’ve now learned how tracking links give recruiters an unconsented view into your behavior. If you want to remain incognito, you cannot blindly trust links in your email.
Unfortunately, even if you manually check every link for consistency, you can still be spied on.
How? Invisible images.
Look again at the email at the top of this page. Do you see the image at image at the end? Of course not – it’s invisible!
Right click -> view page source and you’ll find it, right below the signature.
<img src="https://my-fake-tracker.paon.wtf/item/3" width="0" height="0" alt="" style="border:0;width:0;height:0;margin:0;padding:0">
No border, no width, no height, no title, no space around it…what is this weird image doing here?
Simple.
Even if they’re zero-size, images get loaded as soon as you open your email.
Just like the URLs in the links we saw earlier, the URL in that img src is unique. No message to anyone else, and no other message to you, contains that URL.
As soon as you open this email, the recruiter knows you’ve opened it. No matter how careful you are with links in the email, they now know you’re paying attention, and that it’s worth their time to send you more emails.
In Gmail, you can find these kinds of tracking links using “show original” under the three-dot menu at the top of the messsage. On the new page, search for “img”.
znsrc.com
The tracking URLs I’ve seen in recruiter emails go to a domain called znsrc.com. Here is what they look like in some recent emails I’ve received:
# URLs in tracking links:
https://znsrc.com/c/<random ASCII ID>
# URLs in tracking images
https://znsrc.com/o/<random ASCII ID>
Gross. What even is znsrc? Great question.
In an impressive display of spinelessness, znsrc.com does not even have a landing page to tell me who or what they are. This is what I see when I visit znsrc.com:
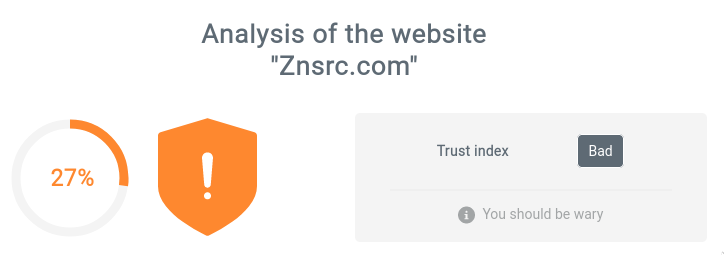
Well if znsrc doesn’t want to speak for themselves, I guess I’ll look at scamdoc instead
I tried looking up the owner using ICANN lookup, but as expected I just see “Identity Protection Service.”
This hacker news thread suggests that these URLs come from Nylas, some kind of recruiting software. My guess is that recruiters write their messages and send them through Nylas. Nylas rewrites all URLs to go through znsrc.com and uses this domain to power a prospect-tracking UI.
Analysis of recent emails
Here is a rundown of all the recruiting outreach I’ve received via email in the last week. I’ve anonymized the companies because for some reason I respect their privacy more than they respect mine.
| Company | tracking links | tracking images | sender |
|---|---|---|---|
| 1 | no | yes | founder |
| 2 | yes | yes | third-party recruiter |
| 3 | yes | yes | third-party recruiter |
| 4 | no | yes | founder |
| 5 | no | no | reply email from recruiter |
| 6 | yes | yes | first-party recruiter |
Honestly, I’m shocked and disappointed by these results. Every outreach email I’ve received has at least contained a tracking image - the most insidious option!
Until I looked, I expected that emails without tracking links generally wouldn’t contain tracking images. I was wrong. Of course, most messages also used tracking links. So far, all of the tracking URLs I’ve seen point to znsrc.
The only exception is a reply email from a recruiter at “company 5”. This is a company that I reached out to first.
What can we do?
Recruiters often use sneaky tricks to invade our privacy. Is there anything we can do to avoid their spying?
I don’t have any perfect solutions, but there are a few technical and behavioral options to consider.
Nuclear option: never use HTML email again
This problem does not exist in plaintext email, since in plaintext email there are no hidden URLs and no images. If you search around, you will see many people recommending against sending or reading HTML email.
I don’t think this is a viable option for most people, for two reasons.
- People like to format their emails using different styles and images, which is not possible in plaintext.
- Gmail does not have a mechanism to open messages in plaintext by default.
If you want to give up html email, it probably means finding a new email client.
Block znsrc.com with your adblocker
uBlock Origin users will no longer have to worry about tracking images from znsrc in their emails, because I got them added to one of its default filter lists.
I would have liked to block the bouncer links too, but this was deemed too disruptive. I think that’s reasonable, but I have all znsrc.com URLs blocked in my personal configuration.
This is a start, but it still requires me to pay attention to new tracking domains appearing in my inbox.
Block external images in emails
If you use Gmail, I suggest enabling this option: “Ask before displaying external images”.
Unfortunately, Gmail does not provide a way to selectively display images in an email. If you decide to load any images, you’re getting all of them – tracking included.
Stop responding to these recruiters
Until I began my deep-dive into this topic, I was aware of the tracking problem but not of its extent. I had already made a habit of ignoring any recruiters with tracking links in their messages.
Unfortunately, I’ve now learned that even emails that look safe often contain invisible tracking images. I don’t think it’s reasonable for me to ignore all recruiter outreach, even with this behavior.
But between ad-blocking and image-blocking, at least I feel relatively secure.
Long press email links on mobile
These tracking links are even more subtle on mobile, where there is no URL overlay before clicking. I’m now in the habit of long pressing-all links. On Android this opens a little popup where you can see the URL and decide whether to follow it.
This isn’t just recruiters!
I think we have all learned to expect some level of tracking online. We know that ads and analytics systems track our habits and use them to build a profile of our habits. When you start paying attention, you’ll see this behavior everywhere.
But somehow, it feels worse – ruder – in this kind of 1:1 interaction.
Honoring good behavior
Let’s close with a list of companies that have cold-emailed me recently without invading my privacy. Here it is: